What is Penetration Testing
Penetration testing is a crucial security procedure that helps companies identify and fix weaknesses in their systems. It begins with a discovery phase, which involves discovering the hosts, ports, and network services within a system. From this discovery phase, the penetration tester can research vulnerabilities and choose an attack method. Then, the penetration tester executes the attack. The end goal of the testing phase is to resolve any vulnerabilities that are discovered during the test.
Penetration testing is sometimes called pen testing or ethical hacking, because the goal is to determine vulnerabilities in a system and test whether a company is adequately protected from these weaknesses. Penetration tests are conducted by ethical hackers to determine how well a company’s security controls are protected from outside intruders. In addition to discovering vulnerabilities, penetration tests can determine how well a company follows security policies and regulations, and the security awareness and skills of its employees.
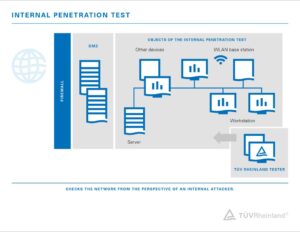
The goal of penetration testing is to identify security flaws in computer systems, networks, and web applications. It mimics real-world attacks on systems and data to determine vulnerabilities and potential hacks. Pen tests are more in-depth than vulnerability assessments, which focus on identifying weak spots and recommending how to fix them. Pentests can be either whitebox or blackbox. It can involve a variety of tools, including a dummy attacker.
What is Penetration Testing and How Does It Work?
Penetration testing can be performed using black box or white box techniques. Black box penetration testing simulates a real exploit of the network and requires a comprehensive network exploration. Both methodologies can be used on different levels of software testing. Businesses that rely on penetration testing as a security measure are likely to stay one step ahead of hackers. They will have a much better understanding of their network than the average user.
Among the three basic pen testing strategies, black box and white box penetration testing offer varying levels of access to the system. While white box testing provides the tester with complete knowledge of the system, black box and gray box penetration testing provide only partial knowledge of the system. The last two methodologies provide a comprehensive security audit that will identify vulnerabilities in the system and fix any vulnerabilities that may be hiding within the system.
In addition to social engineering, phishing attacks are another common form of attack. These attacks usually involve convincing an employee to divulge sensitive information by phone or through email. While network services and social engineering tests are both important, the most common methods of attack are human errors. As such, every staff member must follow certain security standards, such as not mentioning sensitive information in emails. Additionally, security audits can identify flaws in processes that may be insecure.